一些顶级安全专家表示,SolarWinds黑客和COVID-19大流行加速了网络安全支出。
Not only must chief information security officers secure an increasingly distributed workforce, but they now must also be wary of software code coming from reputable vendors, including the very patches designed to protect them against cyberattacks. Organizations are increasingly prioritizing zero-trust approaches, including simplified identity access management, better endpoint protection and cloud security. And while leading solutions in these sectors are gaining momentum, traditional legacy offerings are being managed down from a spending perspecti当前,首席信息安全官不仅要确保越来越分散的员工队伍的安全,他们还必须提防一些来自信誉良好的供应商的软件代码,包括一些本来是用来保护他们免受网络攻击的补丁代码。企业现在更加优先考虑各种零信任(Zero-trust)方法,包括简化身份访问管理、更好的端点保护和云安全等方法。这些领域的领先解决方案的发展势头不错,而从支出的角度来看,传统的老旧产品则日渐式微。
In this Breaking Analysis, we’ll summarize CISO sentiments from a recent Enterprise Technology Research VENN session and provide our quarterly update of the cybersecurity market. In an upcoming episode we’ll be inviting Erik Bradley of ETR to provide deeper analysis on these trends. Here we’ll give you a first look and initial reading of what’s happening in the information security sector as we kick off 2021.
我们将在本文里总结一下最近的企业技术研究VENN会议上CISO(首席信息安全官的英文缩写)的观点,同时也将提供我们对网络安全市场的季度更新。我们还将为读者初步解读一下2021年头两月信息安全领域的态势。
### SolarWinds attack: ‘Like nothing we’ve ever seen’
SolarWinds攻击:“我们从未见过这样的情况”
It’s been covered in the press but in case you don’t know the details, SolarWinds is a company that provides software to monitor many aspects of on-premises infrastructure, including network performance, log files, configuration data, storage, servers and the like. Like all software companies, SolarWinds sends out regular updates and patches. Hackers were able to infiltrate the update and “trojanize” the software — meaning when customers installed the updates, the malware just went along for the ride.
媒体报道过SolarWinds攻击,但假若读者并不知道细节的话,SolarWinds公司提供的软件用于监控企业内部基础架构许多方面的运行,包括网络性能、日志文件、配置数据、存储、服务器等等。SolarWinds和所有其他软件公司一样也会定期发布更新和补丁。而黑客则成功渗透了SolarWinds的更新并植入“木马”,这意味着客户在安装更新时,植入的恶意软件就搭上了顺风车。


The reason this is so insidious is that often hackers will target installations that haven’t installed patches or updates and identify vulnerabilities in the infrastructure that exist as a result. In this case, the very code designed to protect organizations actually facilitated a breach. According to experts, this was quite a sophisticated attack with multiple variants that most believe was perpetrated by the Russian hacker group Cozy Bear, an advanced persistent threat or APT as classified by the U.S. government.
这种情况下的中招很隐蔽,原因是黑客往往会瞄着那些没有安装补丁或更新的系统,然后找到存在的基础架构漏洞。在这种情况下,用作保护组织的代码实际上还促进了漏洞的发生。据专家介绍,这次的SolarWinds攻击属于高级攻击,而且有多个变种,大多数人认为是出自俄罗斯黑客组织Cozy Bear的手笔。Cozy Bear被美国政府归类为高级持久性威胁,或APT。
It is suspected that somehow they phished their way into a GitHub repo and stole username and password access to allow them to penetrate the supply chain of software that is delivered over the Internet. But public information on this attack is still spotty. What is known is that the attackers had been lurking since March of last year and had nine months to exfiltrate troves of data from the U.S. government and numerous other companies, including Microsoft Corp. and Cisco Systems Inc.
据推测,Cozy Bear是以某种钓鱼方式进入一个GitHub库并窃取了用户名和密码访问权限,进而渗透到经互联网交付的软件供应链里。但关于这次攻击的公开信息还是很零散。已经知道的信息是攻击者去年3月就潜伏下来,在9个月的时间从美国政府和众多其他公司(包括微软公司和思科系统公司)那窃取了大量数据。
### What CISOs say about the attack
CISO们对SolarWinds攻击的看法
Last year, right after the attack, friend of theCUBE Val Bercovici of Chainkit said to us on Twitter that he thinks the government hack will have permanent implications on how organizations approach cybersecurity. CISOs seem to agree. Here are some verbatim comments from the CISO roundtable moderated by ETR in late January:
去年我们的CUBE朋友 Val Bercovici of Chainkit在攻击发生后发给我们的推特消息表示,他认为政府被黑将对以后组织如何对待网络安全产生永久性影响。CISO们似乎都同意这个观点。以下是1月底由ETR主持的CISO圆桌会议上的一些评论原文。
> The impact of the breach is profound. It really turned on its head a lot of conventions about cybersecurity.… I don’t think the threat has been exaggerated in the media.
- 这次泄露的影响是深远的,真的颠覆了很多关于网络安全的惯例,我不认为媒体夸大了威胁。
- > We’re now in a situation where we have to monitor the monitors.我们现在所处的情况是,我们必须监控那些监控机构。
- > This attack didn’t have any signatures of a previous attack… so you got down to the code level.这次攻击不具有任何过去攻击的特征……所以是到了代码层面。
- > 80-90% of that code is being downloaded from the internet…. It’s bringing DevOps security processes and making us rethink how to reinvent security.那些代码的 80-90%都是从网上下载的……。事关DevOps安全流程,我们得重新思考如何重塑安全。
### What can be done?
可以做什么?
That’s the question every CISO is wrestling with right now. Security pros will tell you they’re rethinking their practices, tools and approaches, but there’s no one answer.
这是每个CISO现在都在纠结的问题。安全专家会告诉你,他们正在重新考量自己的实践、工具和方法,但没有答案。
Below is a tag cloud summarizing some of what we hear in theCUBE community and in the VENN roundtable from security practitioners:
下图是个标签云,总结了我们在CUBE社区和VENN圆桌会议上从安全从业者那里听到的一些情况。

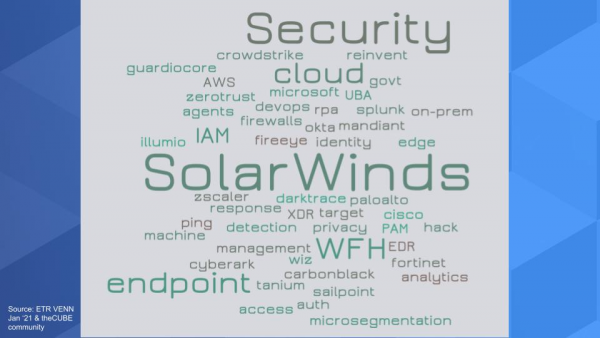
You hear CISOs talk a lot about zero trust and many are leaning into identity access management and PAM, privileged access management. We’re hearing mandates around two factor authentication. We’ve written extensively about identity and firms such as Okta Inc., Sailpoint Technologies Inc. and CyberArk Software Inc. And Microsoft is coming up more and more in this conversation, especially as Okta is seen as setting a price umbrella – there’s definitely some frustration there among CISOs. Auth0, which does authentication as a service, is hitting our radar as well.
可以听到CISO们经常谈论零信任机制,许多人都在倾向于用身份访问管理和特权访问管理,即PAM。我们也听到关于必须用双因素认证的说法。我们过去写过大量关于身份和公司的文章,如Okta公司、Sailpoint技术公司和CyberArk软件公司。微软在这场对话里出现得越来越多了,尤其是业界认为Okta设置了一个价格保护伞,CISO们肯定会有一些沮丧。Auth0是个做身份验证即服务的公司,Auth0也出现在我们的雷达上。
Endpoint security, of course, gets attention as the work-from-home trend has become much more important. You can see it in the growth of CrowdStrike Holdings Inc. and as you’ll see in a moment we’re seeing some traction with VMware Inc. and Carbon Black in the ETR survey data as well as momentum with Tanium Inc.
当然,端点安全受到关注,在家工作的趋势已经变得更加重要。从CrowdStrike Holdings Inc.的增长中可以看到这一点,过一会儿就可以看到,从ETR调查数据中可以看到VMware和Carbon Black以及Tanium的发展势头。
CISOs aren’t going to just rip out what they have so Cisco, especially with Umbrella and Duo, come up in the conversation. As does Palo Alto Networks Inc. We’ve said many times that they’re seen as a thought leader and CISOs like Palo Alto as well as Fortinet Inc. Fortinet buyers tend to be more cost conscious and often midmarket customers.
CISO们不会随便摘掉自己的东西,所以思科(尤其是Umbrella和Duo)出现在谈话中。还有Palo Alto Networks公司。我们说过很多次,他们被视为思想领袖,CISO们喜欢Palo Alto以及Fortinet公司。Fortinet买家往往更注重成本,他们往往是一些中等市场客户。
And so it goes with analytics and micro segmentation and cloud security with Zscaler Inc. and even robotics process automation to automate certain tasks; UiPath Inc. has come up in the conversation more and more in a security context.
分析和微观细分市场方面、云安全方面的Zscaler公司也是这样,甚至实现某些任务自动化的机器人流程自动化公司。UiPath公司 出现在谈话中,还有更多的公司也是在安全场景下出现。
So you look at this tag cloud above and there’s no one answer – as is the case with cyber – lots of tools, lots of disciplines and a very capable adversary who has learned to, as the saying goes, “live off the land,” using your own infrastructure and tooling against you.
因此,看了上面的这个标签云后,没有答案,网络这一块也一样,很多工具,很多学科,还有一个非常有力的对手,已经学会了俗话说的"靠天吃饭",学会了用自己的基础架构和工具来对付你。
### Security budgets are not limitless
安全预算并非无限
The common narrative is that security is a top priority with CIOs and CISOs and budgets will be up. Boards of directors are aware and willing to spend. So let’s look at that.
比较一致的说法是,安全是CIO和CISO的重中之重,预算会增加。董事会意识到了重要性也愿意花费。那我们就来看看这一点。
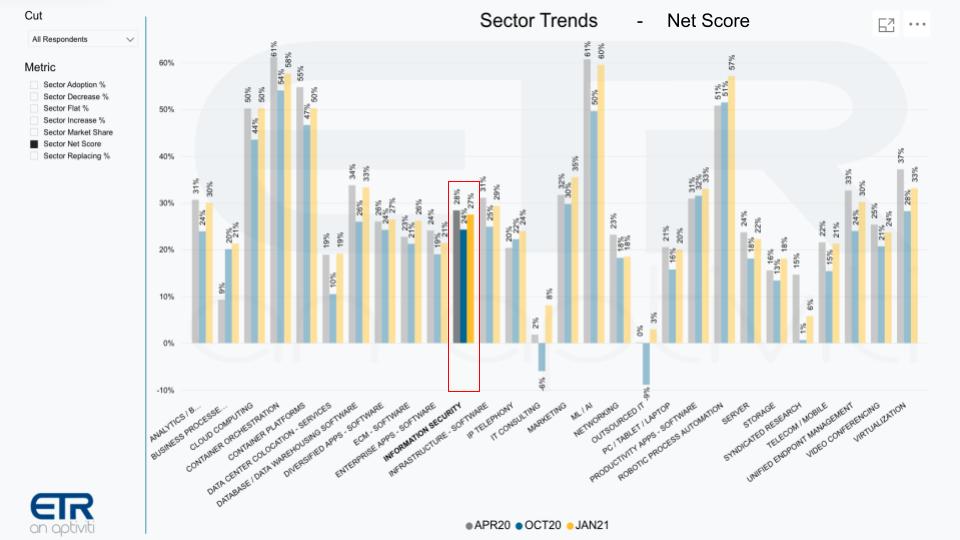
The fact is this is only somewhat true. The chart above shows Net Scores or spending momentum for various sectors across the ETR taxonomy and we’ve highlighted the Information Security segment. Yes, it’s up relative to the October survey, but it doesn’t stand out.
事实是,只是在某种程度上是这样。上图显示了整个ETR分类里各行业的净得分或支出的趋势,我们高亮了信息安全板块。是的,相对于10月份的调查,安全板块的支出是上升了,但并不突出。
Everything’s up, as we’ve reported, coming off a down year in tech spending – minus 4% – and we’re forecasting a plus 6% to 7% increase this year depending on the pace of the recovery. But the point is cyber is one of many budget items and organizations aren’t simply writing a blank check to the CISO.
一切都在上升,就像我们所报道过的,前一年的科技支出下降,是负4%,我们预测今年会有正6%到7%的增长,取决于复苏的速度。但问题是,网络是众多预算项目里的一项,组织并不是简单地给CISO一张空白支票。
### Firms are heavily invested in security already
一众公司已经在安全方面做了大量投资。
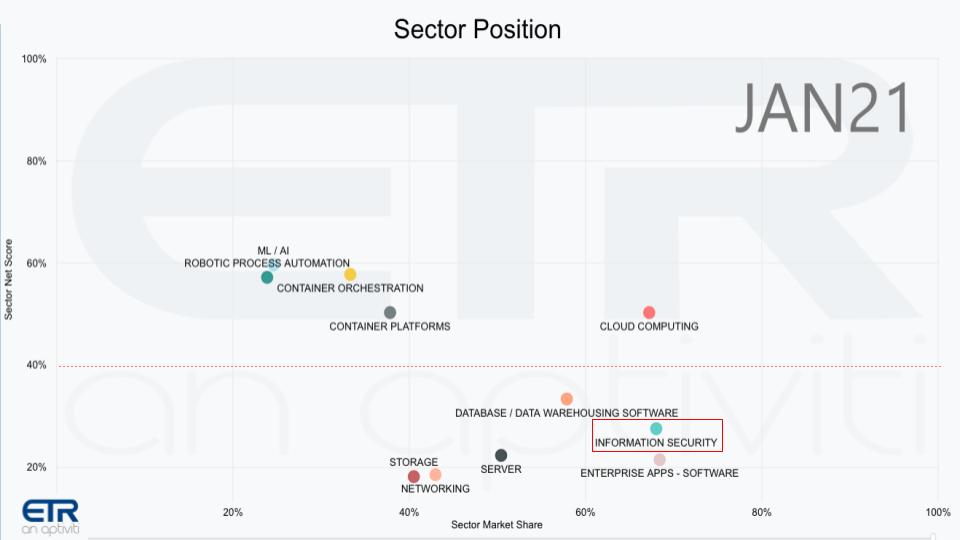

The graphic above shows several sectors in context and we’ve highlighted security in the red box. The vertical axis shows Net Score or spending velocity and the horizontal axis is Market Share or presence in the data set. And you can see that security has a big presence – it’s pervasive, of course.
上图显示了几个行业的场景,我们用红框标出了安全。纵轴显示的是净得分或支出速度,横轴是市场份额或在数据集中的位置。可以看到,安全的位置很靠右,当然,安全无处不在。
But it lags some of the top sectors in terms of spending velocity because organizations have lots of priorities. And of course as you’ll see below, like most mature markets, security has some companies with off the charts spending patterns and others that lag.
但安全在支出速度上却落后一些顶级行业,因为组织有很多的优先事项。当然,正如在下面将要看到的那样,安全领域也和大多数成熟市场一样,有些公司在这方面的支出爆棚,也有一些公司的支出模式落在后面。
#### Vendors in identity, endpoint and cloud have spending momentum
身份识别、端点和云计算领域厂商具消费动力
Below you see that same XY graphic and we’ve plotted a number of selected security players:
下图是同样的XY坐标图,列出了一些选定的安全玩家的数据。
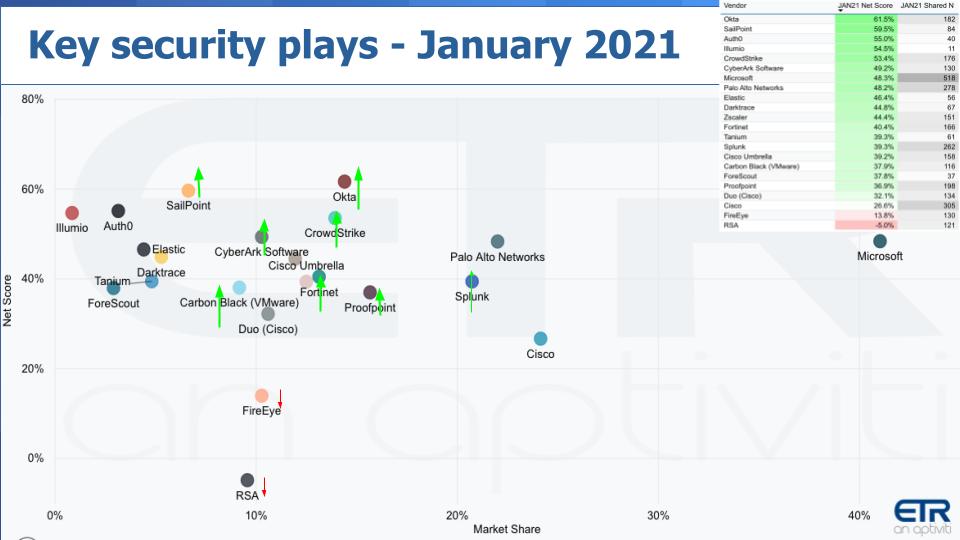
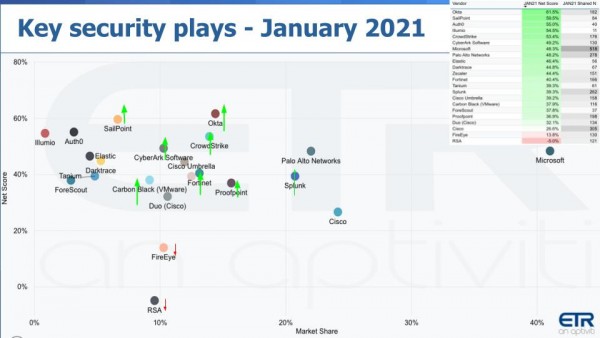
Several points stand out from the above data:
从上图可以看出几点。
* First **Microsoft** , as usual, is off the charts to the right and amazingly, has an elevated Net Score of 48%.
- 首先,微软一如既往,远远地抛开其他商家处于图右边,令人惊奇的是,净得分也提升了48%。
* **Okta** continues to lead this pack as it has in the last several surveys with a Net Score of 61.5%, up from last quarter’s survey.
- Okta在过去几次调查里一直处于领先地位,净得分为61.5%,比上一季度的调查净得分高。
* Okta, **Crowdstrike** , **CyberArk** , **Fortinet** , **Proofpoint** and **Splunk** , all up nicely from last quarter’s survey.
- Okta、Crowdstrike、CyberArk、Fortinet、Proofpoint和Splunk均比上一季度调查的净得分有很好的增长。
* Also we want to highlight **Carbon Black**. The company’s Net Score last quarter was 23.9% with 134 mentions and this quarter its Net Score shot up to nearly 38% — a meaningful and noticeable move for VMware’s $2.1 billion acquisition that it made in the summer of 2019.
- 我们还要特别提一下 Carbon Black。该公司上个季度的净得分为23.9%,被提及134次,本季度的净得分飙升至近38%。VMware在2019年夏天花21亿美元收购Carbon Black,这样明显的增长也是不负这次的收购。
So we see a number of companies with momentum, which stems from a rebound in tech spending generally but also the shift in security spend that we’ve highlighted. And you can see a couple of legacy security firms losing spending momentum – FireEye Inc. and RSA in particular, but there are many others in the ETR data set that are in the red zone.
我们看到了一些公司的好势头,一方面是源于科技支出的普遍反弹,但也源于我们强调提出的安全支出的转变。我们也可以看到有几家传统安全公司失去了支出动力,尤其是FireEye公司和RSA公司,但在ETR数据集中还有许多其他公司也处于红色区域。
### Microsoft, Palo Alto Networks, Okta and CrowdStrike: notable momentum and market presence
微软、Palo Alto Networks、Okta和CrowdStrike:显著的好势头和市场位置。
Let’s dig deeper into the data and the vendor performance.
下面我们来深入了解一下数据和厂商的表现。
Below is a view of the data we first showed you in 2019. The tables depict the Net Score (spending velocity) and the Shared N which identifies the number of mentions within the sector and is an indicator of presence in the market. The leftmost chart is sorted by Net Score and the right hand chart is sorted by Shared N. To make the cut and get into this chart, we required a vendor to have had at least an N of 50 mentions in the sector within the survey.
下表是我们在2019年首次展示的数据视图。这张表显示了净得分(支出速度)和分享N指标,分享N指标表示在业界被提及的次数,是个市场存在指标。左边的表是按净得分排序,右边的表按分享N指标排序,入选被考虑之列并出现在图表里的供应商在调查时间范围内至少在业内被提及50次。
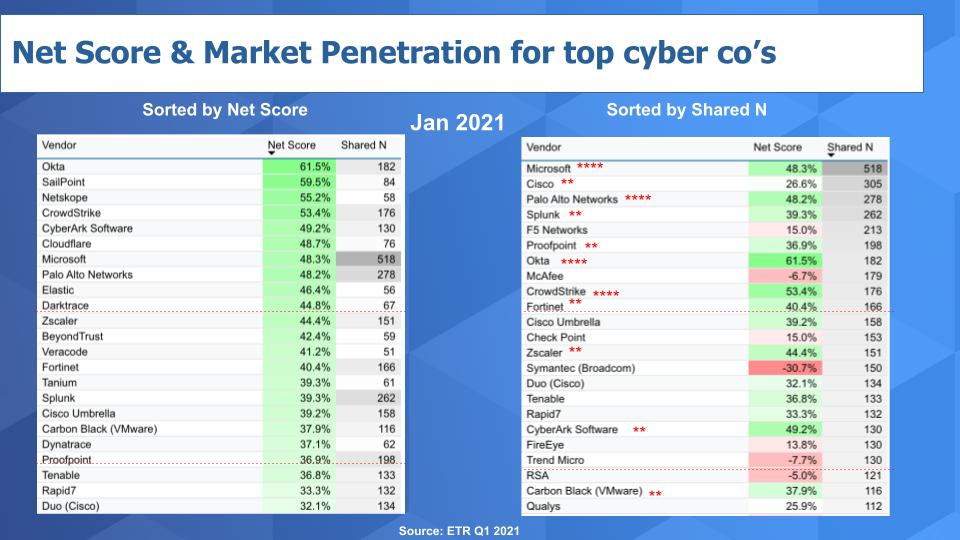
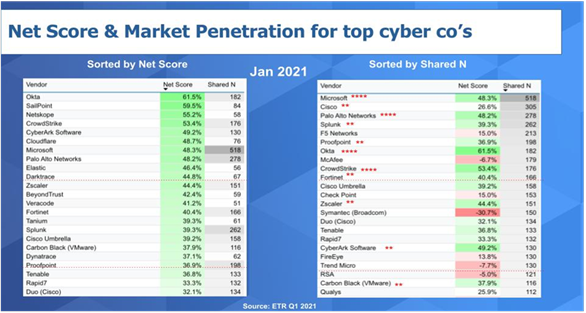
You can see on the leftmost chart that Okta (61.5%) and Sailpoint (59.5%) lead in Net Score and Microsoft has the largest presence in the sector (518 Shared N) along with Cisco (305) and Palo Alto (278).
可以从左边的表看到,Okta(61.5%)和Sailpoint(59.5%)在净得分上领先,微软在业界的存在指标数最大(518共享N),思科(305)和Palo Alto(278)排第二、第三。
#### Four-star and two-star companies
四星级公司和两星级公司
Something we started two years ago was if a vendor shows up in the top 10 for both Net Score and Shared N, we anoint them with four stars. So **Microsoft** , **Palo Alto** , **Okta** and **CrowdStrike** are the four cybersecurity vendors that fall into the four-star group.
我们在两年前开始用星级评等方法,如果一家厂商的净得分和分享N指标都出现在前十名,我们就会给四颗星。所以微软、Palo Alto、Okta和CrowdStrike四家都是四星级网络安全厂商。
And we give two stars to those companies that make the top 20 in both categories. So **Cisco** because of Umbrella and Duo, **Splunk** , **Proofpoint** , **Fortinet** , **Zscaler** , **CyberArk** and **Carbon Black** (now owned by VMware). Carbon Black is new to the two-star list thanks to its rapid rise in Net Score.
而那些在这两个类别中进入前20名的公司则获得两颗星。Cisco(由于Umbrella和Duo的关系)、Splunk、Proofpoint、Fortinet、Zscaler、CyberArk和Carbon Black(现属VMware)都是两星级网络安全厂商。Carbon Black由于净积分的快速上升成为两星榜单新厂商。
#### A quick aside on Carbon Black
关于Carbon Black的一个小插曲
At VMworld 2019, Pat Gelsinger told theCUBE that he felt like he got a great deal picking up Carbon Black for $2.1 billion.
在2019年的VMworld活动上,Pat Gelsinger告诉theCUBE,他觉得花21亿美元的价格拿下Carbon Black是一笔好的大买卖。
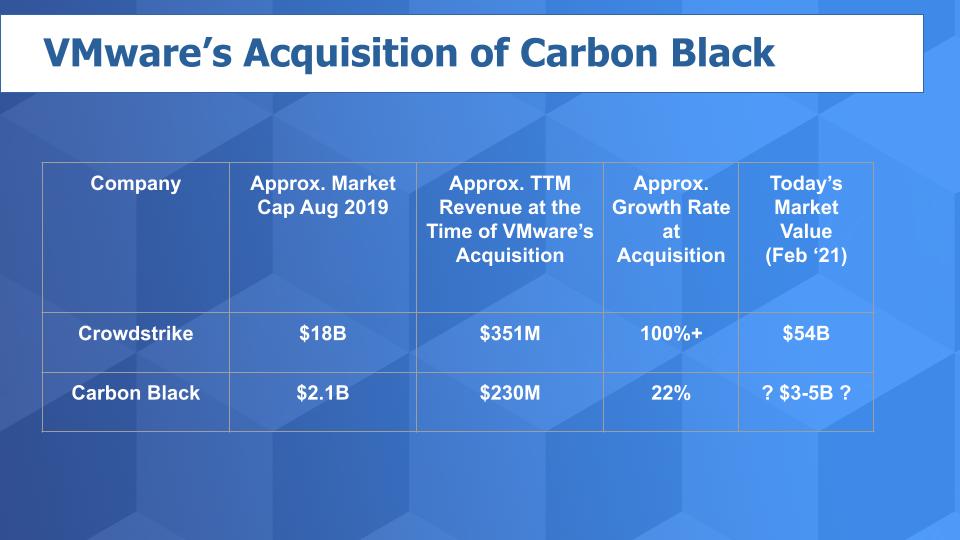
His logic was in part based on the valuation of CrowdStrike, a Carbon Black competitor. At the time CrowdStrike, as you can see on the chart below, had a valuation that was nine times higher than that of Carbon Black. And you can see from the trailing-12-month revenue that CrowdStrike was a bigger company by more than $100 million, but the real story was the company’s growth at more than 100%. CrowdStrike at the time was growing much faster than Carbon Black’s 22%, justifying a significantly higher relative value.
他这样说的逻辑一部分是基于Carbon Black竞争对手CrowdStrike的估值。CrowdStrike当时的估值(如下图)是Carbon Black的9倍。而且可以从尾部12个月的营收里看到,CrowdStrike是一家规模更大的公司,营收比Carbon Black高一亿多美元,但故事的核心是CrowdStrike的增长达100%。CrowdStrike当时的增长速度远高于Carbon Black的22%,证明其相对价值明显更高。

Of course, the thinking from VMware was that it could pick up Carbon Black at a discount to the market leader and inject growth and profitability into the asset by bundling into VMware’s increasingly capable security offerings. VMware created a cloud security group headed by Carbon Black Chief Executive Patrick Morley, which underscores a commitment to the sector.
当然,VMware的想法是可以以低于市场领导者的价格折价收购Carbon Black,然后通过将其捆绑到VMware日益强大的安全产品上为该资产注入增长和盈利能力。VMware创建了一个由Carbon Black首席执行官Patrick Morley领导的云安全集团,凸显了在该领域的承诺。
Now in VMware’s recent earnings call, it said Carbon Black had “good” bookings performance. Who knows exactly what that means, but if it were significantly more than 22% (Carbon Black’s growth rate at acquisition time), our guess is that VMware would have been more effusive. So let’s assume that since the acquisition Carbon Black growth has been flattish relative to its growth at acquisition as VMware figures out how to integrate the company.
VMware在最近的财报电话会议上表示,Carbon Black的预订表现 "良好"。谁都不知道这到底是什么意思,但如果增长率明显超过22%(收购时Carbon Black的增长率是22%),我们猜VMware的溢美之词可能会更夸张一些。我们不妨假设自收购后,Carbon Black的增长相对于收购时的增长更趋向于平缓,VMware在这一段时间不是在想办法整合这个公司嘛。
Nonetheless, we would still peg its valuation as having increased substantially since the time of acquisition – perhaps in the $3 billion-to-$5 billion range. So it’s a nice pickup for VMware in our view, which has a good track record of acquiring companies and monetizing the assets. And we think the value of Carbon Black inside of VMware will likely grow from here. Further, the ETR data on Carbon Black is encouraging.
尽管如此,我们仍会认为Carbon Black的估值自收购时起已大幅上升了,或许在30亿至50亿美元之间。所以在我们看来,对VMware而言是宗不错的收购,VMware在收购公司及将资产货币化方面有良好的记录。而且我们认为,置于VMware内部的Carbon Black的价值可能会从这里开始增长。此外,Carbon Black的ETR数据也令人鼓舞。
### Cybersecurity valuations continue to skyrocket for the leaders
领军企业的网络安全估值持续飙升
Let’s look at how the valuations in this sector have changed since before COVID.
我们来看看自新冠以来这个行业的估值是如何变化的。
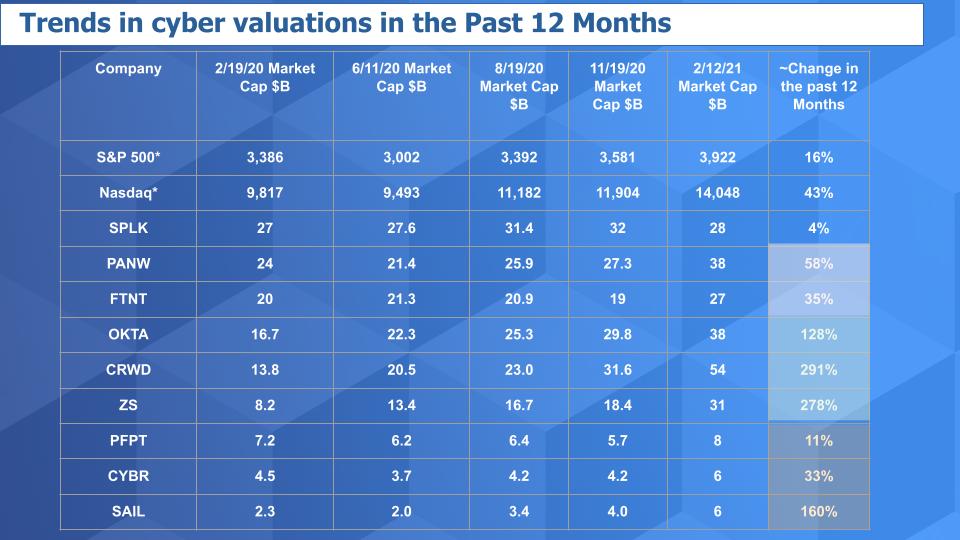
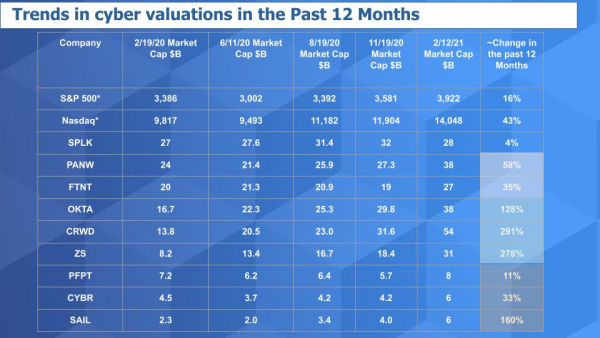
Above is an updated view of our valuation matrix since just before the pandemic hit the U.S. in earnest. You can see the S&P is up 16% from that timeframe and the Nasdaq composite up 43%. Now look at the others. Only Splunk really hasn’t seen a big uptick in valuation. And Proofpoint’s valuation hasn’t kept pace. But the others have either risen noticeably, such as CyberArk and SailPoint, bounced up such as Palo Alto, held nicely such as Fortinet or exploded as with Crowdstrike, Okta and Zscaler.
上表是我们的估值矩阵最新视图,时间段为自美国爆发新冠大流行病前夕以来。可以看到,标准普尔指数比那个时间段上涨了16%,纳斯达克综合指数上涨了43%。现在来看看其他的股票。只有Splunk的估值真的没有大的提升。Proofpoint的估值也没有跟上。但其他公司要么涨幅明显,如CyberArk和SailPoint,要么反弹上涨,如Palo Alto,要么保持良好,如Fortinet,要么大爆发,如Crowdstrike、Okta和Zscaler。
So one would think Carbon Black as a VMware asset has done pretty well along with these names and will make long-term contributions to VMware.
那大家会大致会觉得VMware的资产Carbon Black也会和这些公司一样做得很好吧,会对VMware做出长期的贡献。
In addition, we would expect that the tech spending rebound this year combined with the heightened concerns over the SolarWinds hack and the tectonic shifts from the accelerated work-from-home and digital business transformation will continue to bode well for many of these names… for some time.
此外,我们预计,由于今年科技支出的回升,加上对SolarWinds黑客事件的高度关注以及从在家工作和数字化业务转型构造性转变的加速,这些公司将持续向好......在一段时间内。
### Factors to watch in cyber
网络方面的关注因素
As we exit the pandemic and are experiencing a new digital reality, cyberthreats have never been greater. Each January if you looked back on the prior year you’d be able to say the same thing for the past several decades. And the reality is that the budget allocations and subsequent spending on cyber are asymmetric to the economic risks. In other words, the $125 billion or so spent on cybersecurity doesn’t square with the trillions of dollars in value lost each year to cybercrime. We don’t spend enough as it is and probably can’t spend our way out of this problem.
我们退出大流行,同时也在经历一个新的数字现实,这时的网络威胁空前严重。每年的一月,如果回顾上一年的情况,我们就会说出和过去几十年同样的话。而现实情况是,网络预算分配和后续支出与经济风险是不对称的。换句话说,1250亿左右的美元花在网络安全上,每年因网络犯罪而损失达数万亿美元的价值,二者并不对等。我们现在花的钱还不够多,但可能也无法靠花钱解决这个问题。


CISOs have to balance their legacy installed base security infrastructure with the shift to zero-trust, accelerated endpoint, new access management challenges and an ever-expanding cloud. And much more. Very few have the benefit of a blank sheet of paper.
CISO们必须平衡在自己的传统安装基础安全基础架构以及向零信任的转变、加速端点、新的访问管理挑战和不断扩展的云之间取得平衡。还有做更多的事情。很少有人能够像一张白纸一样没有过去的包袱。
Lack of talent remains the single biggest challenge for organizations, which are stretched thin — making investments in automation a trend that is not going to abate any time soon.
人才的缺乏仍然是企业面临的最大挑战,企业已经捉襟见肘了,因此在自动化上的投资就成为一种趋势,这种趋势是不会在一段时间内减弱的。
In cyber, all the cliches apply: There is no silver bullet. There is no rest for the weary. The adversaries are well-funded and extremely capable and they have to succeed only once to create a business disaster for an organization, whereas an organization must succeed every minute of every day. So expect more of the same with no end in sight in terms of complexity, fragmentation and Whac-A-Mole approaches to fighting cyber crime.
在网络方面,各种陈词滥调仍然有效:不存在灵丹妙药。无暇喘息,仍要疲于奔命。对手的资金充足,能力也极强,他们只需成功一次,就能给一个组织带来商业灾难,而一个组织每时每刻都必须成功。因此,准备好应付更多相同情况的出现,打击网络犯罪时的复杂性、分散性和“打地鼠”(Whac-A-Mole)法等等都是没有尽头可言的。
It hurts to say this, but it just means the fundamentals for this sector just keep getting better. That’s bad news, but it’s the reality for organizations trying to protect their data — and it’s good news with lots of opportunities for investors.
这样说很痛苦,但这样说只是意味着这个行业的基本面正在不断改善。而对于试图保护自己数据的组织来说,这就是现实。而这对投资者来说是个好消息,机会多多。








